There are six methods of deletion to securely delete files. Each method offers another security level. The deletion varies in time due to the security level of the method used. The method "Lowest security" is preset.
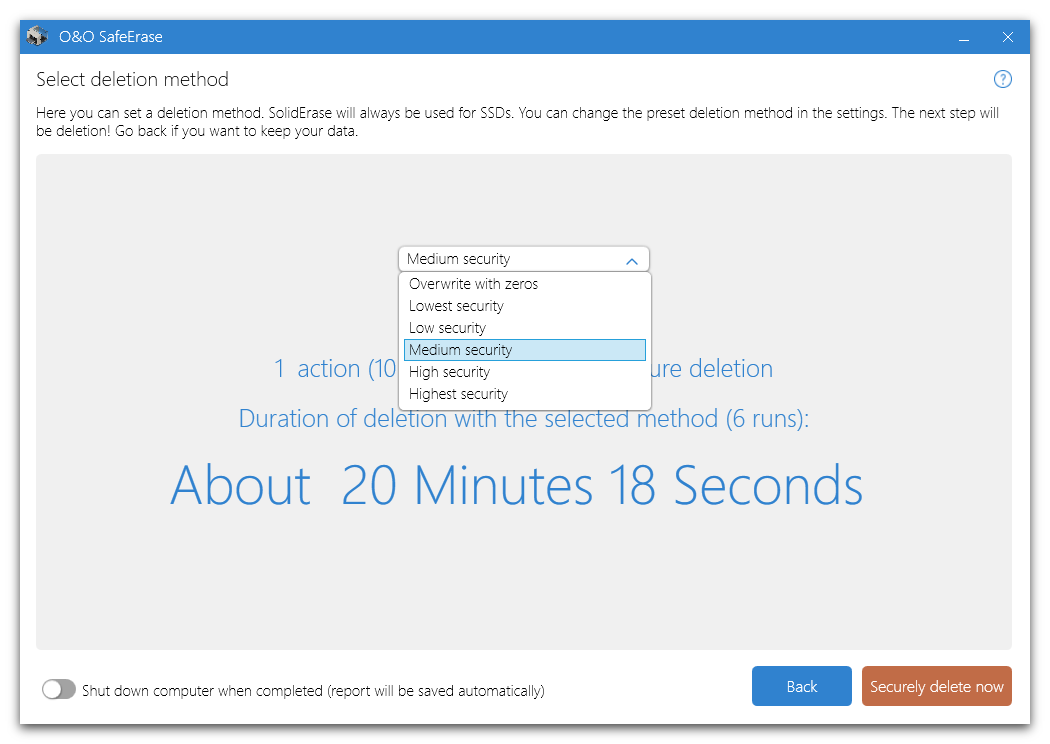
Method of deletion
Even data securely deleted with the lowest security level cannot be restored using commercial data rescue programs. These methods are useful if you want to delete private pictures or videos before selling your computer. Data Ssecurely deleted with medium or high security levels cannot be restored even by data rescue labs or from specialized offices. Use this method when deleting sensitive company or financial data for instance.
Higher levels require a longer amount of deletion time as the lower levels. The higher the level is, the higher number of deletion cycles have to be completed. You can now set the PC to run the deletion process and then shut down automatically.
The display of time remaining is only an approximation. The actual amount of time needed for deletion can vary significantly, depending on the system’s capacity and condition of the hardware. This indicator basically serves to illustrate the differences in time needed for deletion according to the volume of data and the deletion method selected.
Six methods of deletion
Highest Security (35 runs)
The method that offers the highest level of security is based on a process developed by Peter Gutmann and presented in his article “Secure Deletion of Data from Magnetic and Solid-State Memory”. In this method, deleted data is overwritten by a series of 35 different deletion cycles that are executed in a random order.
High Security (7 runs)
The method for high security is based on the January 1995 'National Industrial Security Program Operating Manual' by the DoD. In this seven cycle variation (DoD 5220.22-M ECE), data is first overwritten three times with DoD 5220.22-M (E) Standards, then with a specific random value, and finally once again with DoD 5220.22-M (E).
Medium security (6 runs)
This method for medium security conforms to the standards of the German BSI as described in the “BSI IT Baseline Protection Manual”. Data is overwritten with a random value and then with this values complement. This procedure is completed with new random values three times.
Low Security (3 Cycles)
The method is based on the "National Industrial Security Program Operating Manual“, NISPOM (US DoD 5220.22-M) the DoD from January 1995. It proceeds with 3 runs (DoD 5220.22-M E): data is first overwritten with a fixed value, then with the complement of that value, and finally with a random value. The advantage lies in the speed with which this method proceeds to securely delete data.
Lowest Security (1 run)
This method is quick, but offers very little security in the deletion of data. Using this method, data is overwritten with random values in one cycle.
Overwrite data with zeros
This method is the fastest, but offers very little security in the permanent deletion of data. The selected files will be overwritten with zeros.